Year-End Security Tech Trend Takeaways
With all the launches, refınements, hype and promotion wrapped up, what were 2022’s key security technology advancements? Experts from top suppliers sort it out and translate the opportunities.

(Image: denisismagilov/stock.adobe.com)
Looking back at 2022, it strikes many as a year that flew by super quickly. It’s a stark contrast to 2020, a year that seemingly stood still as if in suspended animation. And for many, 2021 served as a bridge between the two that led to a slow but steady road to recovery. The security industry was among those sectors fortunate enough to hold steady throughout the changing tides of the pandemic.
Steve Burdet, manager of solutions management, Axis Communications, sums it up well, “COVID-19 was a major global disruptor that impacted every industry. However, despite its negative impacts, it allowed the security industry to realize resiliency and the value of technology.”
With 2022 about to be in the rearview mirror, take close scrutiny of the types of technologies and services that gained traction among both dealers/integrators and their end-user clients. The latter was drawn to several clear-cut security and operational advantages while the most successful of the former — recognizing that demand and expanded use cases — nimbly stepped into the fold with suitable solutions.
Tech Atop 2022’s Leaderboard
Video Surveillance
Artificial intelligence (AI) was a key contender. Corey Plender, vice president of product and customer experience, Alula, concurs, noting that cameras are becoming more powerful, turning them into video security sensors and allowing users to have a better understanding of what is happening around them. “This can be anything from facial recognition as someone approaches a door, fall detection, or showing pets and vehicles near their premises. When an alarm is triggered, based on observing a pattern of images via the camera, the video solution automatically records the event. Video verification can lead to a timelier response and help mitigate false dispatches.”
Jason Burrows, sales director for IDIS America, points out, “Not only does AI improve safety and security and allow for a more proactive approach, it spares operators from having to monitor multiple streams and eliminates the need to dispatch security officers to investigate alarms caused by harmless environmental factors. This means organizations can reduce staffing levels in control rooms and redeploy personnel to more rewarding, frontline tasks that improve stakeholder engagement.”
Most of the significant new technologies and capabilities in video surveillance come from advancements in systems-on-chip, says Burdet. “We’re able to put more advanced technologies on edge chipsets than ever before. And while this is true with every advancement in processing, it is only recently that edge chipsets can support AI accelerators.”
He references that this breakthrough has opened the door for a longer “futureproofing” of current models when coupled with the ability to support a containerized framework of applications. This means that even as applications become more complex, the ability to divide them into smaller containers that require AI accelerators will allow these current models to run even future applications to some extent.
“In addition to adding AI capabilities for analytics, this same intelligence can be used to focus on the image processing — improving low light and wide dynamic range processing as well as intelligent compression techniques,” adds Burdet. “Ultimately, this will improve performance of the camera and the accuracy of the data it creates. New chipsets are also able to run more advanced cybersecurity applications — both third-party and manufacturer applications — which helps the edge device better meet the network needs of the organization.”
Access Control
Derek Cleveland, access product manager, Speco Technologies, says the use of two-factor authentication has significantly increased the security of access systems. “Locking the doors using access control hardware is the first line of defense, but advances in AI for video surveillance has increased this defense by keeping people out who try to scam the system. In the past, if a potential intruder found a credential on the ground near a controlled door, there is a chance they would be able to enter the building unobstructed.”
There are many notable developments in access control technology, but the most significant include mobile credentials, Cloud-based and hybrid solutions, and data encryption, adds Rob Druktenis, program manager, access control at Axis. Each of these capabilities offer end users added convenience, flexibility and reliability.
“For starters, since the vast majority of people own a smartphone, the use of mobile credentials — via QR code or Bluetooth — with multifactor authentication is simple, cost-effective and more secure than traditional badges or cards, which can be stolen or lost,” he says. “Similarly, the Cloud can offer more flexibility with regard to managing permissions, system updates, and data at multiple sites. And hybrid access control schemes allow users to take advantage of different methods to effectively authorize access in each layer of IoT architecture.”
Druktenis also notes that, when it comes to an access control system, the end user’s physical security and data protection are at stake, so cybersecurity is of utmost importance. Accordingly, advancements in end-to-end solutions can offer seamless encryption from card reader to controller to server — providing end users greater protection and peace-of-mind.
Intrusion Detection
Tom Mechler, regional marketing manager, Bosch, reports that the shift to IP and cellular communications continues to be significant for the intrusion market. “While this has been a challenge to the intrusion industry for several years, the 3G sunset has brought it to light once again for dealers and installers who need to upgrade their customers’ communication technology before the supporting networks are discontinued,” he says. “Integration also continues in importance as customers expect systems to work with one another to provide synergy. Intrusion, access, video and public address systems should work as one to provide the best solutions for end customers.”
Cleveland adds that, by using analytics such as facial recognition to allow or deny a credential scan, that intruder turns into a would-be intruder because they have the right credential, but the wrong face to use it with. In the context of intrusion detection, the same principle can be applied to controlled gates with license plate recognition. By requiring a match of two different factors, one after the other, it becomes much easier to secure all entry points, he says.
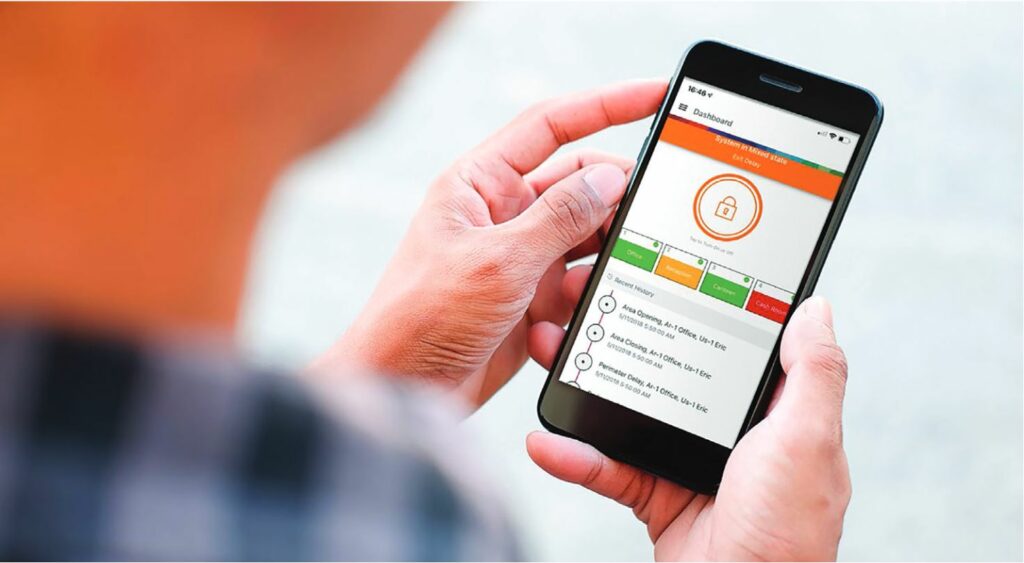
The Bosch Security Manager mobile app allows users to manage all aspects of their intrusion systems including arming/disarming; adding/deleting/changing user pass codes; and the ability to receive alerts when needed.
New Tech Drives New Demand
As new capabilities and applications emerge so do new opportunities for dealers and systems integrators. In the realm of video surveillance, according to Burrows, customers are shifting faster than ever to NDAA-compliant equipment, encouraged further by the impending FCC ban on new equipment authorizations that has been passed by the U.S. House of Representatives. “Those federal businesses that are impacted by the ban, such as some of the world’s biggest logistics and warehousing organizations, are rapidly migrating to NDAA-compliant solutions. And NDAA-compliant equipment is also being adopted beyond those that need to comply today, as we’re seeing similar demand across luxury retail, hotel chains, and cannabis operators.”
Plender is seeing increased demand for small business property monitoring cameras in high-traffic areas outside and inside facilities. It is also important to have an NVR system where video footage may be stored and managed, as well as proximity-based AI.
Burdet adds, “We see a lot of interest in improved perimeter protection and products that help deter vandals before they can complete their task. These include audio solutions to warn intruders, smart detectors for sensing intrusions and indicators to physically demonstrate something has occurred. We’re also seeing demand for solutions that can provide business efficiencies and process monitoring capabilities. These combine smart sensors — cameras, radars, etc. — with analytics and other systems to provide deeper insights, proactive responses or quicker reactions.”
Speco’s Cleveland says the two solutions end users are seeking the most are access and video integration, and remote management. “By integrating surveillance cameras with an access control system, incidents can be timestamped and then are easy to find on the NVR. Additionally, live video of entrances may be called up quickly during an event, making it easy to unlock the door for a friend or alert the appropriate party to the presence of an intruder in real-time. And remote management capabilities allow end users to control multiple properties from the convenience of one office. They like to have the ability to lock and unlock doors and add and delete card holders when not onsite.”
Druktenis adds that today’s end customer is savvier and more forward-thinking when it comes to their investment in technology. “End users want greater system integration through VMS, analytics and other enterprise solutions in order to maximize their investment. In the same regard, there’s an increased demand for integrating physical and logical access control. This is driven by a need to manage cardholders and users more securely by using a shared database. And mobile credentialing gained popularity during the pandemic as a touchless entry solution. Users then recognized it as a cost-effective and highly secure access solution, so it remains in high demand.”
Cloud connectivity, especially for remote command, configuration and control of intrusion systems are what Mechler reports they’re seeing the most demand for. “COVID has changed the landscape for many commercial customers who are still transitioning from a remote workforce to a hybrid environment. This means their buildings are not occupied in the way they were pre-COVID, so customers expect to be able to control and administer their systems remotely. Thus, use of smartphone apps for this purpose continues to grow.”
How to Leverage New Opportunities
Security dealers and partners need to evaluate the many video surveillance options and provide their customers with the best options based on their needs, Plender advises. “Small business owners and homeowners are inundated with video surveillance options and are looking to the experts to direct them in the right direction. There is a lot of information out there and it is up to the security dealers to understand what makes the most sense for that application and present that solution.”
Kyle Heironimus, vice president of advanced products for DMP, encourages dealers and integrators to use technology and automation that is focused on saving labor, noting it’s shortsighted to save a few dollars on solutions that don’t incorporate automation as they’ll still lose customers because of labor-related backlogs.
“Look at your cost breakdown if you don’t already. You will probably find that you spend more on labor than equipment. You might actually be able to save money by spending more on equipment and saving on labor.”
Integrators also have an opportunity to educate end users that security technology doesn’t have to be seen as a grudge purchase, Burrows says, pointing out that cameras are no longer just security devices for reviewing footage after a crime or incident. “AI now makes security teams proactive in terms of preventing crime and intervening before health and safety incidents and accidents occur to reduce losses, injuries and insurance claims. And in retail and hospitality, AI-powered video is also giving sales and marketing teams valuable in-store and customer intelligence using people-counting, heatmapping and queue management tools.”
Burdet advises anyone in the industry to become more familiar with analytics, Cloud connectivity and interconnected systems, citing them as more than just trends. He views them as technologies adding significant value for end users to solve challenges, improve their businesses and gain competitive advantages. “These technologies will continue to gain greater sophistication and prominence. For dealers and systems integrators, these new technologies are the way to increase business and become more involved with customers so as to retain long-term relationships as a trusted advisor.”
Integrators should encourage their customers to be as safe as possible, Cleveland says, pointing out that showing end users they have their best interest in mind can help build trust and prompt sales. “From a monetary standpoint, more equipment from a combined access control and surveillance install means more money in a dealer’s pocket. Additionally, analytics and two-factor authentication can be charged as premium services and may even offer RMR opportunities.”
Druktenis emphasizes the importance of dealers staying up-to-date on the latest technologies. Accordingly, as the trusted expert, they must educate customers on the more secure and convenient credential technologies. “It’s important to convey the value of modernizing and switching to these options,” he says. “Make the business case for the advantages of newer, more advanced systems and the possibilities they present when it comes to integrating other technologies and systems.”
Intrusion systems are often in place for many years, Mechler notes, and the systems that customers have in their facilities may not support the technology required to allow for features such as remote-control smartphone apps. This offers the integrator the opportunity to upgrade these systems to provide this capability. “Upgrading systems to provide new technology gives the dealer or integrator the opportunity to increase RMR through cellular services and the use of smartphone apps.”
Erin Harrington has 20+ years’ security industry media experience. Contact her at [email protected].
If you enjoyed this article and want to receive more valuable industry content like this, click here to sign up for our FREE digital newsletters!

Security Is Our Business, Too
For professionals who recommend, buy and install all types of electronic security equipment, a free subscription to Commercial Integrator + Security Sales & Integration is like having a consultant on call. You’ll find an ideal balance of technology and business coverage, with installation tips and techniques for products and updates on how to add to your bottom line.
A FREE subscription to the top resource for security and integration industry will prove to be invaluable.







